 by May 14, 2019
by May 14, 2019
No question, preparing for a network audit can be a time-consuming, labor-intensive ordeal that can take weeks (maybe months). If you’re like most enterprise network teams, by the time you’ve assembled everything for the auditors, it’s all obsolete because your network has changed.
Compliance is a moving target. The volume, velocity, and variety of change in today’s networks is unprecedented. And that’s not going to subside anytime soon. We’ve gone from an environment of continuous change to one of instantaneous change.
Trying to ensure compliance “by hand” is an exercise in futility. With the seemingly endless parade of mandated regulations (PCI DSS, HIPAA, SOX, GLBA) and industry standards (ISO 27001/2, NIST) requiring your compliance, automation is the only way you can be continuously ready to pass your network audit with flying colors.

Top Reasons for Network Audit Failures
Network audits are a different animal than financial audits. (Back in the day, I worked for the State Auditor’s Office and wrote up hundreds of audit reports.) Financial auditors basically look to see if you have adequate internal controls (what we’d call “policies”), then investigate a statistically significant sample of transactions (usually about 1-2%, depending on the size of the organization). It’s pretty cut-and-dried. Either everything is accounted for according to Hoyle, or it isn’t. Even if there was some funky accounting somewhere along the line, most often the auditors will be satisfied if things got straightened out and you’re in compliance by the time of the audit.
Not so with network audits. IT managers need to show not only that the network meets regulatory standards right now but also that it did so within any given time frame in the past. Further, most regulatory compliance standards mandate that you are taking proactive measures to secure sensitive data and close vulnerabilities.
Trying to ensure compliance “by hand” is an exercise in futility. By the time you’ve assembled everything for the auditors, it’s all obsolete because your network has changed.
Most network audit problems can be traced back to two general causes:
- It’s difficult to prove compliance — even if you’re operating within the “rules,” you don’t have up-to-date documentation that backs you up.
- You run into compliance drift: it’s hard to keep track of how all the constant changes to firewalls, policies, rules, and exceptions affect compliance, so your network reverts to an out-of-compliance state.
A corollary to 2a: while one team (SecOps) is responsible for defining the “golden rules” and security policies of the network, a different team (NetOps) is responsible for making changes to the network. And the two teams don’t always have an effective means to collaborate with each other.
What Auditors Expect, and Why That’s a Problem
No matter what compliance regulation or standard they’re verifying, auditors want to see documentation — lots of documentation.
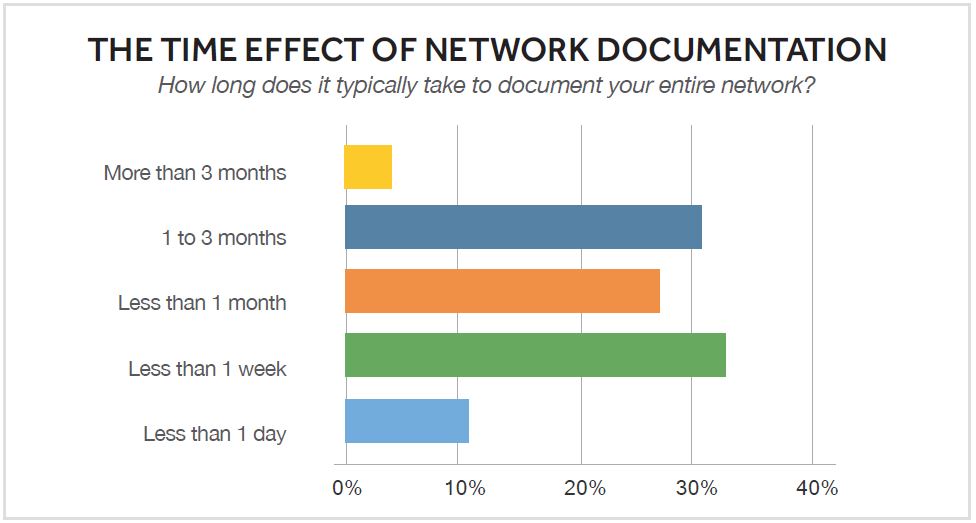
Usually, this documentation comprises Visio diagrams and design documents in Word. The problem most organizations face is that their diagrams are almost always out of date. In our recent survey, 61 percent of engineers said that up to half of their network documentation is outdated.
Unlike a finance team, which has a comptroller or accountant keeping the books on a daily basis, network teams rarely have someone dedicated solely to documenting every change. We all know we should document everything, and none of us has the time. (We’ll get to it later, but “later” never comes.) And the biggest reason is that the vast majority (87%) of teams still rely on manual methods to create and update diagrams, and manual documentation simply takes too long.
While there are tools out there to help generate simple topology diagrams, auditors will also ask for documentation on underlying design and policies: firewall rules, access lists, policy-based routing, configuration hardening, and more (both current and historical). And they increasingly expect this documentation to be supplied on demand.
What auditors are fundamentally looking for is assurance that sensitive data is safeguarded. They’ll check whether your devices are secured — proper authentication, password encryption, exec timeouts, telnet disabled, etc. — and that the network is segmented into subnets that restrict access to certain information so that only specific groups can get to it.
That’s a lot of data to collect, analyze, and document. Not to mention all the possible paths that application traffic could take. Not just today, but last week, last month — whatever window of time the auditors choose to test. Laying your hands on the documentation to prove compliance is at best a challenge; at worst, it’s virtually impossible without a few weeks’ head start.
Providing auditors with comprehensive documentation as soon as they ask for it makes things go much smoother. Nothing puts an auditor “on high alert” more than seeing auditees having to scramble around to pull things together.
From experience, I can tell you that providing auditors with comprehensive documentation as soon as they ask for it makes things go much smoother. Nothing puts an auditor “on high alert” more than seeing auditees having to scramble around to pull things together. And all too often, one of the biggest documentation challenges is the most basic: generating an accurate inventory report. Many enterprises struggle to know exactly what devices they have across their network. As inventory documentation is invariably one of the first things auditors request, you don’t want to start off behind the eight ball.
Dynamic Documentation Automatically Supplies the “Evidence”
NetBrain ensures that you have everything you need for the auditors available at your fingertips. It all starts with deep intelligent discovery of the network. Using not only SNMP but also the CLI, NetBrain’s discovery engine builds a data model of your entire network that in essence automatically documents everything — config files, route tables, CDP/ARP/MAC/STP tables, inventory information, and more. A recurring network discovery (called a benchmark) ensures that this “digital twin” of your entire network remains accurate and up to date. These recurring benchmarks (you define how often you want to run them) provide a repository of log data that can be referenced during network audits to demonstrate compliance over time.
This deep network intelligence is leveraged to create data-rich network maps dynamically, with unparalleled precision and speed. These Dynamic Maps are created on demand to generate any kind of diagram an auditor could possibly want to see: bird’s-eye overview diagrams, campus maps, and especially live and historical maps of traffic flow and link utilization. In fact, all compliance regulations require you to keep normal state and failed state diagrams for all your data centers and WAN paths.
This type of map is difficult to create manually because it means logging into a variety of devices to check routing information in order to understand real-time traffic flows and link utilization. Building this kind of map from scratch and by hand is error-prone, static, and likely doesn’t reflect the live network closely enough to be reliable.
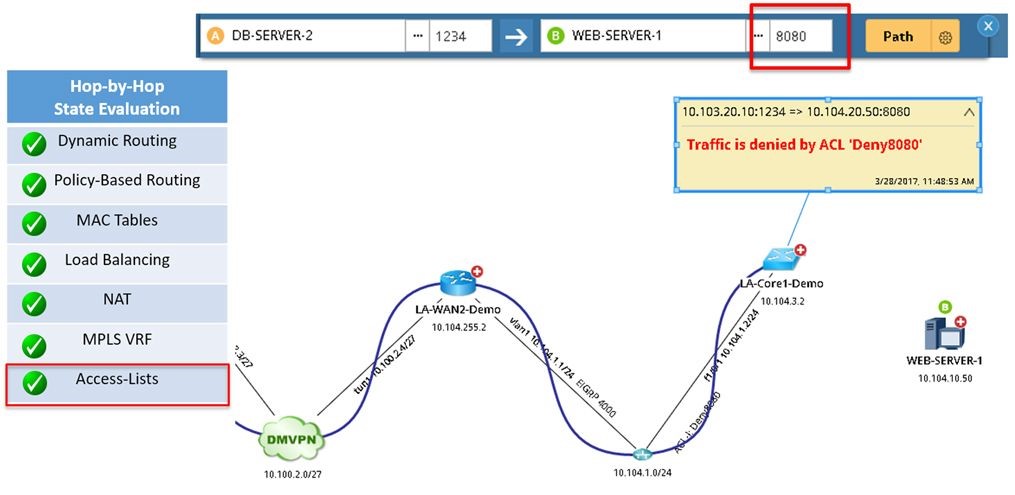 NetBrain’s A/B Path Calculator maps any path, including showing ACL configuration.
NetBrain’s A/B Path Calculator maps any path, including showing ACL configuration.
That’s where NetBrain’s A/B Path Calculator is invaluable. Simply enter a source and destination address, and NetBrain dynamically maps out the entire path end to end — through firewalls and load balancers, across virtual devices. NetBrain’s recurring benchmarks mean that in the future, you can pull up historical flow diagrams as well.
These maps are dynamic, meaning not only that they auto-update on the fly but also that you can drill down into virtually any details. Whereas icons on static diagrams are merely pictograms representing the existence of a device, the icons on Dynamic Maps are interactive and data-driven — clicking on them pulls up information captured in the “digital twin” data model.
Say a PCI compliance auditor is looking to validate credit card transaction paths. NetBrain performs a comprehensive analysis at every hop along the path, taking into consideration PBR, ACLs, NAT, and more. All this information is displayed and documented right on the Dynamic Map.
This is exactly the kind of documentation auditors are looking for, and you can export Dynamic Maps to Visio (which is how most auditors will require them) with just a single click. NetBrain eliminates tons of manual network audit preparation effort by enabling you to batch-export Visio diagrams to a central repository and keep them updated on a predefined schedule, as well as inventory reports in Excel and design documents in Word.
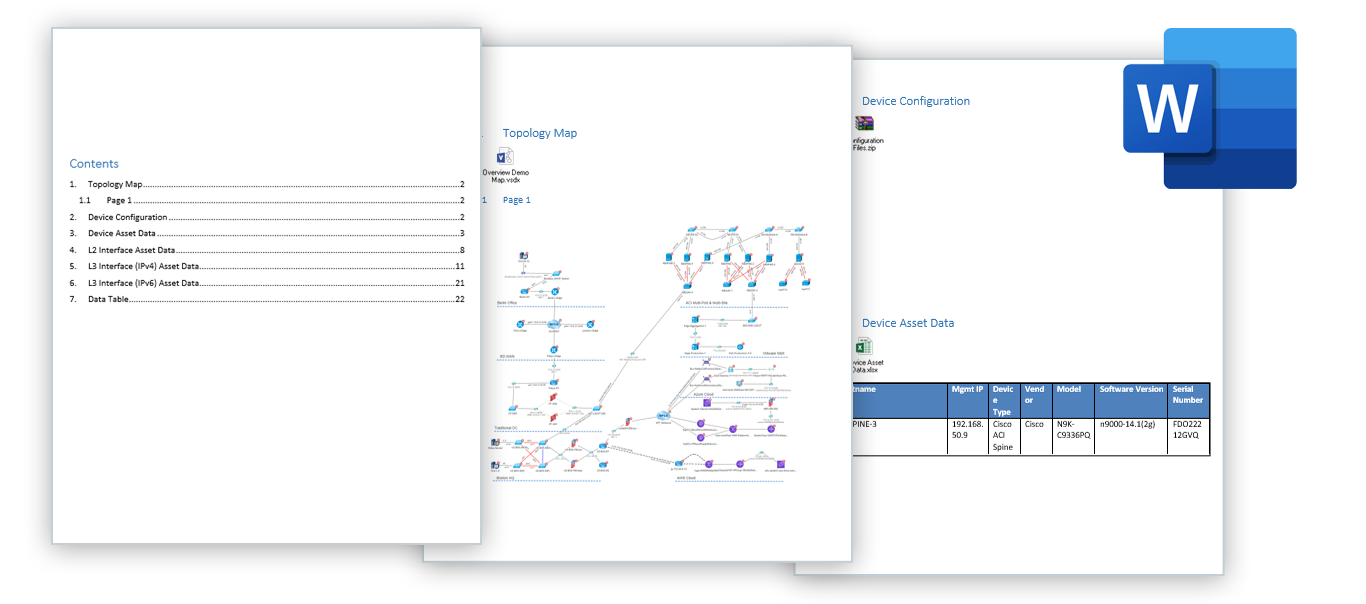 One-click export of Dynamic maps to Visio, inventory reports to Excel, and highly customizable design reports to Word.
One-click export of Dynamic maps to Visio, inventory reports to Excel, and highly customizable design reports to Word.
Automation Prevents Drift to Ensure Continuous Compliance
Compliance requirements mandate that companies take proactive measures to prevent, detect, contain, and correct network security violations, attacks and other vulnerabilities. Just how proactive you need to be is not especially well defined, but the best approach is a systematic process that pursues continuous compliance, a state where compliance with requirements is attained and then perpetually maintained. Not only does continuous compliance improve your overall security posture, but it helps relieve IT teams of the resource-intensive burden of preparing for a network audit — because you’re already ready.
Where you run into trouble with achieving continuous compliance is the difficulty in validating every network configuration against a set of golden rules (device passwords are encrypted, timeouts are configured, no vendor defaults are still present, etc.). In anything other than the smallest network, there’s no way engineers can analyze every configuration manually. And custom scripts speed up the process only marginally — they break at scale and are difficult to maintain.
That’s where NetBrain automation comes in.
NetBrain’s automation can validate every network configuration against your security policies (“golden rules”) by looking at every device’s configuration, searching for predefined rules within each device, and reporting any device that’s non-compliant.
NetBrain’s vulnerability assessment technology explained in 3 minutes
Once you’re in state of compliance, automation can help you stay there. As mentioned, it’s not uncommon for organizations to “drift” back into noncompliance, given the dynamic nature of the modern network. In fact, we’ve reached a tipping point where configuration changes are happening at warp speed, and security teams are struggling to detect compliance discrepancies. It has to been done with automation.
Every time there’s a configuration change, you can have an Executable Runbook automatically run a programmable set of procedures to collect and analyze specific network data to ensure that the network adheres to your golden rules. Without NetBrain, these steps would normally be executed manually in the CLI, one device at a time. Dozens of these compliance checks are available out of the box in NetBrain, but you can also custom-define the Runbook steps to meet specific in-house or regulatory compliance needs.
In the example below, the Runbook will automatically check router authentication, password encryption, SSH access, etc., but other steps could include looking at SNMP community strings, interface port security, ASA failover status — any information you could check manually via SNMP or the CLI can be retrieved automatically by a Runbook. Runbooks may even include design guides and best practices to help enforce security best practices going forward.
An event management system can even be configured to auto-trigger a vulnerability assessment at the instant a change takes place.
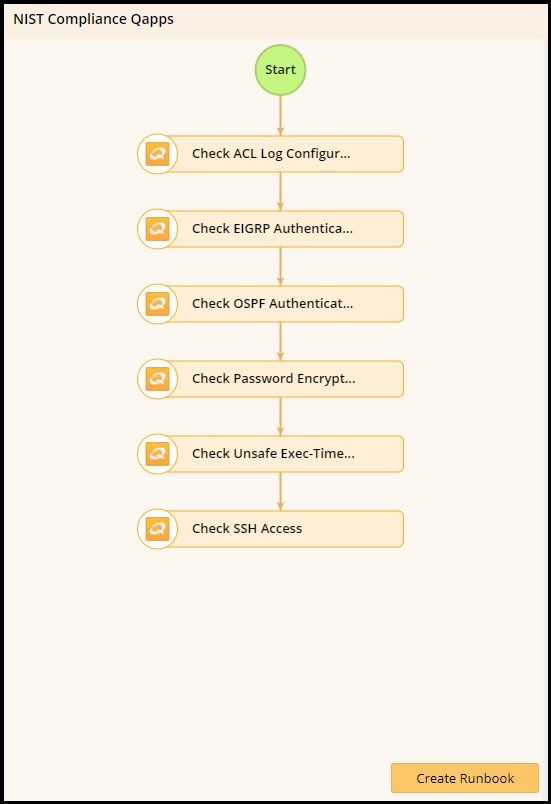 Executable Runbooks automatically validate network parameters against security and privacy compliance checklists.
Executable Runbooks automatically validate network parameters against security and privacy compliance checklists.
All Runbook results are saved right inside the Dynamic Map, and each map is accessible via public URL and easy to share. Finally, SecOps and NetOps have a common interface for collaborating and sharing information.
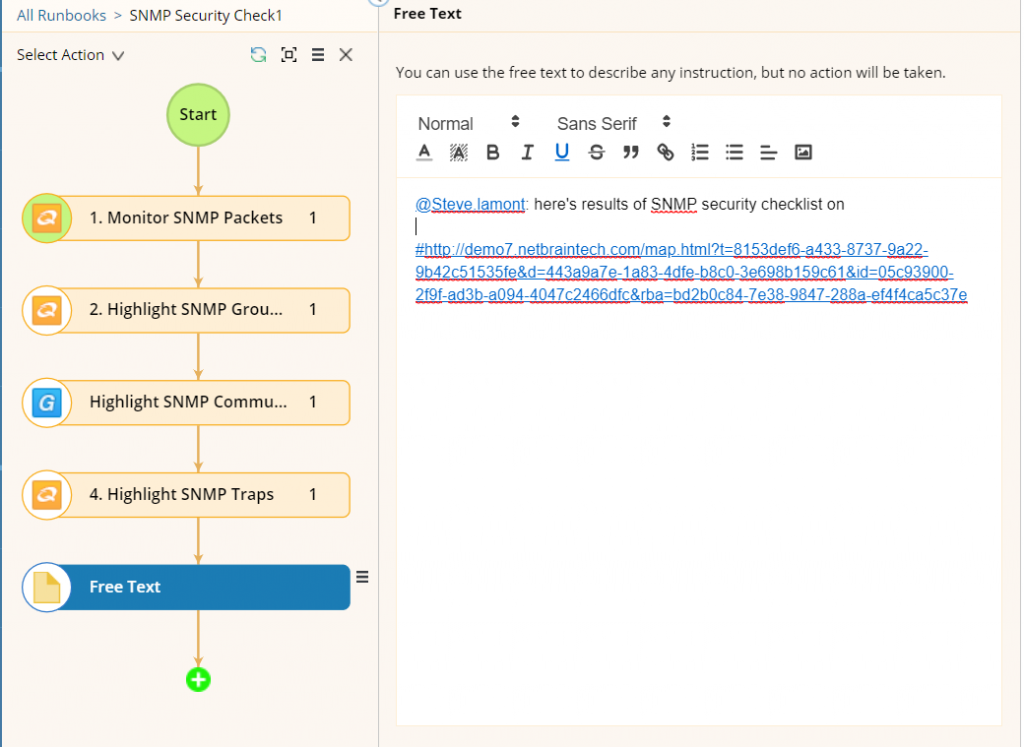 NetBrain Runbooks make it easy to collaborate and share information by alerting specific users and hyperlinking to specific maps.
NetBrain Runbooks make it easy to collaborate and share information by alerting specific users and hyperlinking to specific maps.
Conclusion
Preparing for a network audit shouldn’t be like going on a crash diet where you achieve short-term weight loss, only to regain it all back within a few weeks. Yet that’s what usually happens with many organizations. When network audit time rolls around, a big chunk of the team has to focus on aligning policies to pass a specific network audit, pulling together a ton of documentation, and performing security assessments (in addition to everything else on their plate). If that’s a one-and-done effort, you’ll go through the same thing the next time, and the time after that. . . .
That approach eats up a lot of time and resources, and doesn’t necessarily make your network more hardened against cyber threats. A better approach is to maintain continuous compliance with your security policies (which are aligned to the mandated regulations) so that you’re always in compliance and ready for a network audit at a moment’s notice.
Ensuring continuous compliance using manual methodologies is virtually impossible in today’s networks. They’re too complex and move too fast for humans to keep up without help. Automation is that help and, really, is the only way to ensure that no change is throwing your network out of compliance. NetBrain’s Runbook Automation can systematically check your network for compliance, with the results auto-documented. When the auditors show up asking for proof of compliance (current and historical), you have it all logged and accessible at your fingertips.
That’s the surest way to ace your next network audit.
[su_box title=”What’s the difference between a network assessment and a network audit?” box_color=”#279dd8″]
While it might seem merely a matter of semantics — and in fact they’re very similar — the two terms are not interchangeable.
A network audit is performed to ensure that an organization’s current network security is legally compliant with mandated regulations.
A network assessment goes beyond determining strictly whether or not specific criteria are met, and identifies potential performance problem areas, technical vulnerabilities, and weaknesses in policies and practices (e.g., bandwidth bottlenecks, security flaws, and under- or overutilized resources).[/su_box]


 NetBrain’s A/B Path Calculator maps any path, including showing ACL configuration.
NetBrain’s A/B Path Calculator maps any path, including showing ACL configuration. One-click export of Dynamic maps to Visio, inventory reports to Excel, and highly customizable design reports to Word.
One-click export of Dynamic maps to Visio, inventory reports to Excel, and highly customizable design reports to Word. Executable Runbooks automatically validate network parameters against security and privacy compliance checklists.
Executable Runbooks automatically validate network parameters against security and privacy compliance checklists. NetBrain Runbooks make it easy to collaborate and share information by alerting specific users and hyperlinking to specific maps.
NetBrain Runbooks make it easy to collaborate and share information by alerting specific users and hyperlinking to specific maps.