What is Network Hardening?
Network hardening refers to the configuration of systems to minimize vulnerabilities and reduce the risk of cybercrime. Cyber attacks have evolved to become more covert and targeted. So, your network services and systems need reinforcement to become more resilient to attacks. Cybersecurity hardening secures networks from external security threats and internal vulnerabilities. It first identifies security vulnerabilities such as access, programs, outdated network devices, default passwords, and unencrypted data, and like a door left wide open, it closes them.
Network hardening techniques that once involved blocking unauthorized network access have since become outdated, as they only focused on firewalls. Modern attacks bypass perimeters because of the increased remote access by employees and third-party access.
By automating network operations, administrators can enhance network device hardening by disabling unused ports and services, installing software updates and security patches, implementing strong access controls, enforcing secure firewall configurations, and monitoring network traffic for malicious activities.
Operating system hardening strengthens network defenses and keeps the systems resilient by making it harder for hackers to gain unauthorized network access or move laterally within the network once they have breached perimeter security controls.
Why is Network Hardening Important for Your Organization?
Network hardening is essential for protecting organizational assets from cyber threats and data breaches. The frequency and complexity of cybercrime have seen financial firms lose around USD 12 billion in the last twenty years, threatening global financial stability.
Hardening network security helps keep your networks safe from external and internal attacks. Hackers constantly probe networks for weak points like open ports and unpatched systems. With more sensitive data leaving the office to remote places and the over-reliance on cloud storage, network hardening should be a primary focus.
Access to data on business networks results in compromises that could lead to reputational damage, financial losses, and legal liability. Hardening strengthens network defenses to mitigate risks, meet compliance needs, and help ensure network operations run without security incidents.
On top of safeguarding an organization’s network against malicious attacks, server hardening has additional benefits. A network hardening checklist helps improve performance and security as hackers can exploit fewer exposed weaknesses. Hardening also streamlines auditing and compliance tasks by reducing the number of programs.
With a hardened system, there are fewer chances of potential entry points for hackers, strengthening the entire network and enhancing your organization’s security posture.
The hardening network process comprises three key phases, each serving unique objectives and presenting distinct challenges. Let’s delve into each phase to gain a comprehensive understanding of the network hardening process and its significance in ensuring network security:
- Document the Existing Network Design and Configuration
To effectively address security vulnerabilities, the first step is gaining a comprehensive understanding of the network’s design and configuration. Unfortunately, many organizations struggle with outdated or incomplete network documentation, which hinders their ability to identify potential risks, like telnet enabled, accurately. Automating the process of network documentation can provide a dynamic view of the network, enabling real-time insights into security and application traffic flows.By leveraging tools like Dynamic Maps, organizations can automate the documentation process, offering edge-to-cloud visibility, detailed asset reports, and comprehensive network diagrams. Additionally, advanced features such as NetBrain’s A/B path calculator can validate access lists and firewall policies to ensure proper traffic filtering across the network.
- Identify and Remediate Security Vulnerabilities
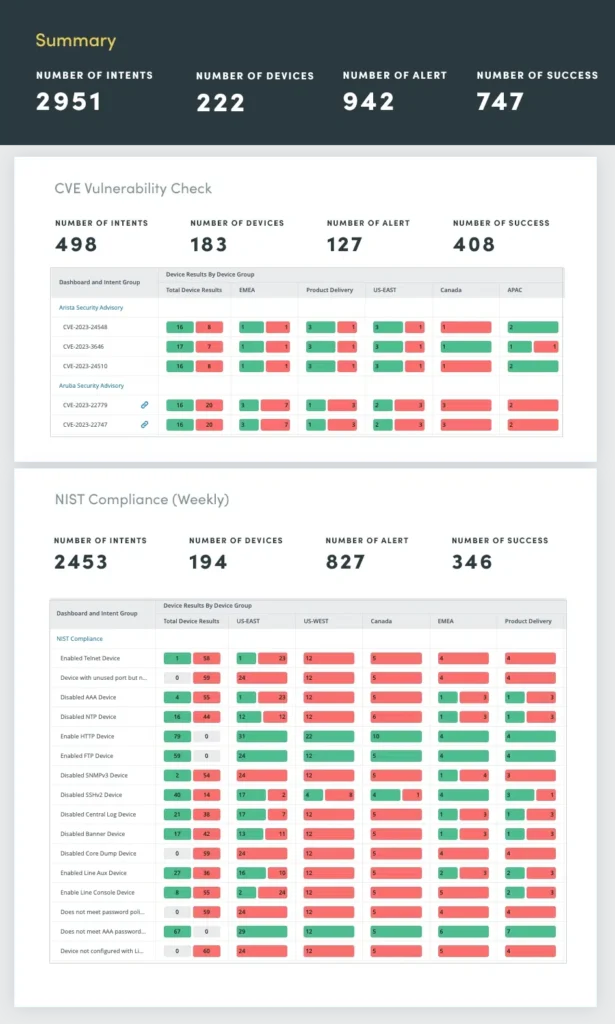
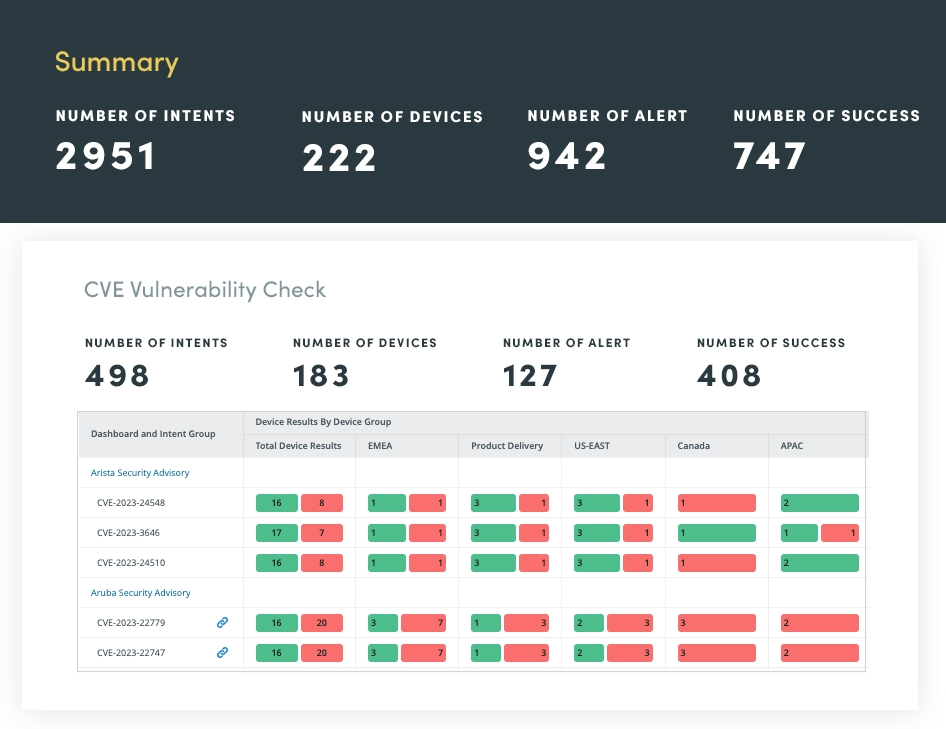 The second phase of network hardening involves identifying and addressing security vulnerabilities. Traditionally, this process relied on manual analysis or custom scripts, both of which had limitations. Manual analysis was time-consuming and prone to errors, while custom scripts lacked portability and were challenging to maintain.
The second phase of network hardening involves identifying and addressing security vulnerabilities. Traditionally, this process relied on manual analysis or custom scripts, both of which had limitations. Manual analysis was time-consuming and prone to errors, while custom scripts lacked portability and were challenging to maintain.
Automation tools such as NetBrain’s NextGen network automation offer a more efficient approach. NetBrain’s NextGen can continuously validate network configurations against a predefined set of “golden rules” encompassing security best practices. These rules can include encryption of device passwords, proper configuration of timeouts, consistent settings for HA pairs, and prevention of insecure protocols. By automating the validation process, organizations can proactively identify and rectify any deviations from the desired security posture.
- Safeguard Against Future Vulnerabilities
The final phase of hardening a network focuses on establishing robust practices and processes to safeguard against future vulnerabilities. It is imperative to ensure consistent adherence to security policies across all network teams within the organization. By leveraging the golden rules identified in the previous phase, security teams can create no-code automation that serves as comprehensive and actionable guides for future remediation efforts.This automation encompasses intents, or design guides, that enforce security best practices, providing clear guidelines on configuration and regulation standards (like NIST), access controls, and recommended protocols. Implementation engineers can utilize these runbooks to execute vulnerability assessments whenever network changes or new application installations occur. By automating regular vulnerability assessments, organizations can proactively identify and address any potential security gaps or deviations from the established security standards.Automation tools like NetBrain’s NextGen event management system play a pivotal role in streamlining the hardening network process. These tools can be configured to automatically trigger vulnerability assessments whenever changes are made to the network. By automating the assessment process, organizations can ensure that any modifications or updates made to the network infrastructure align with the predefined security standards, reducing the risk of introducing vulnerabilities inadvertently.Network hardening is a crucial and ongoing practice for organizations dedicated to protecting their networks from ever-evolving cyber threats. By diligently following the three essential phases of network hardening—documenting network design, identifying vulnerabilities, and implementing security practices—organizations can significantly enhance the security posture of their networks.
Leveraging automation tools, such as NetBrain’s NextGen network visualization tools, simplifies and accelerates the process, enabling proactive enforcement of security measures and ensuring a resilient network infrastructure.
Embrace the power of network hardening strategies, like automation, to safeguard your network from potential threats and mitigate the risks associated with today’s dynamic threat landscape.
For further guidance and expertise on network hardening and how it can effectively strengthen your organization’s cybersecurity initiatives, do not hesitate to reach out to our team of experts. We are committed to helping organizations build robust and secure networks that can withstand the challenges posed by modern cyber threats.
Partner with NetBrain
Your systems and network contain valuable data that we want to prevent cybercriminals from accessing. Don’t let the integrity of your network be compromised. Instead, let system hardening provide a robust system that keeps attackers out and safeguards your internal operation systems. Implementing hardening methods will keep your organization safe and compliant with regulations and ease auditing.
At NetBrain, we stand out as the sole No-Code Day-2 network automation platform. Our team of experts provides you with network hardening best practices, such as automation and visibility, to simplify tasks, maintain compliance, and strengthen your network infrastructure.
We’ll help you automate continuous network-wide assessments to identify vulnerabilities and misconfigurations, address the problems, and harden the network. Let our end-to-end network operations tools, from network mapping to network visualization, help provide you with a centralized view of the full network topology, including assets, interfaces, routes, and more.

 The second phase of network hardening involves identifying and addressing security vulnerabilities. Traditionally, this process relied on manual analysis or custom scripts, both of which had limitations. Manual analysis was time-consuming and prone to errors, while custom scripts lacked portability and were challenging to maintain.
The second phase of network hardening involves identifying and addressing security vulnerabilities. Traditionally, this process relied on manual analysis or custom scripts, both of which had limitations. Manual analysis was time-consuming and prone to errors, while custom scripts lacked portability and were challenging to maintain.