Attack SecOps Challenges Head On
Outdated Documentation
Out-of-sync topology maps, golden config templates, and device config change histories increase risk and make it difficult to address risk and compliance.
Drift From Golden Standards
Insufficient protections for critical assets, data, and networks can leave you vulnerable to hackers, data leaks, and disruptions.
Response & Recovery Time
Delayed restoring of systems and data after a cybersecurity incident can lead to extended downtime and penalties.
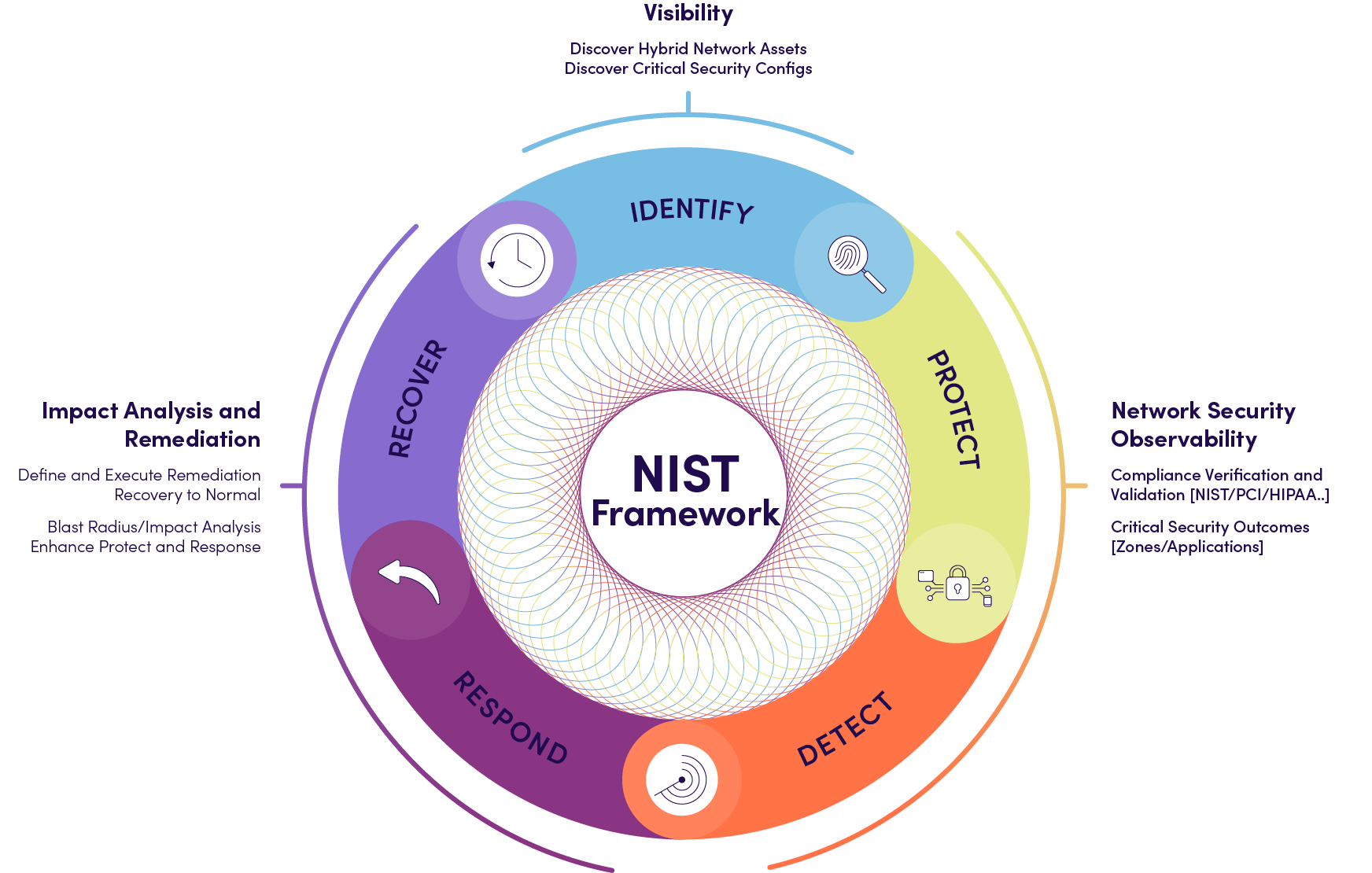
3-Step NIST Framework Approach
Visibility
Discover hybrid network assets and critical security configurations.
Observability
Using the power of always-on automation, NetBrain checks help maintain compliance verification and validation for mandates and regulations including NIST, PIC-DSS, HIPAA, etc., without human intervention. Achieve critical security outcomes for zones and applications.
Impact Analysis & Remediation
For every response, there should be a recovery plan. NetBrain uses maps, Triggered Automation Framework, and AI Co-Pilot to triage any security incident to aid your diagnosis.
Response & Recovery Time
3 Angles of Network Security Observability

Device Security
Understand CVE, NIST, and EOL/EOS device vulnerabilities to lock down network security.
Application Security
Understand how traffic flows across zones and if any path deviates from its golden application path. Auto-remediate the drift with one click.
Zone Security
Enforce what traffic is allowed or disallowed between DMZ and production zones for every tier of all critical applications.

Enforce Security at Every Level
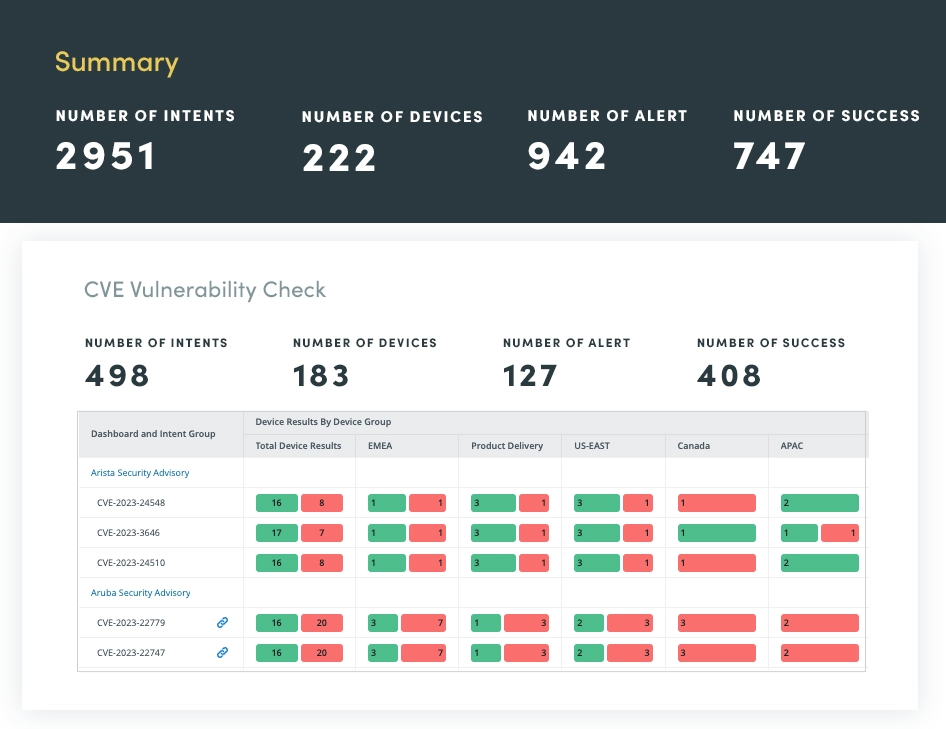
NetBrain ensures precision at every step. Continuously validate critical configurations like AAA, ACLs, and TACACS against your golden templates to eliminate vulnerabilities before they arise.
- Spot Issues Instantly: Actionable dashboards provide quick insights for teams, from summaries for leadership to detailed engineer reports.
- Compliance Guaranteed: Eliminate risky configurations like “any-to-any” firewall policies with precise, enforced security rules.
- Secure by Design: Define, validate, and enforce rules like segmentation to keep your network aligned, compliant, and resilient.



Seamless Security Changes
NetBrain removes the guesswork from network security changes:
- Before the Change: Predict disruptions before they happen. Map out potential impacts to paths and rules so nothing catches you off guard.
- During the Change: Lock in accuracy. Validate every change to ensure it works as intended and stays aligned with your security policies.
- After the Change: Stay ahead of threats. Turn one-time checks into ongoing assessments that keep your network secure around the clock.


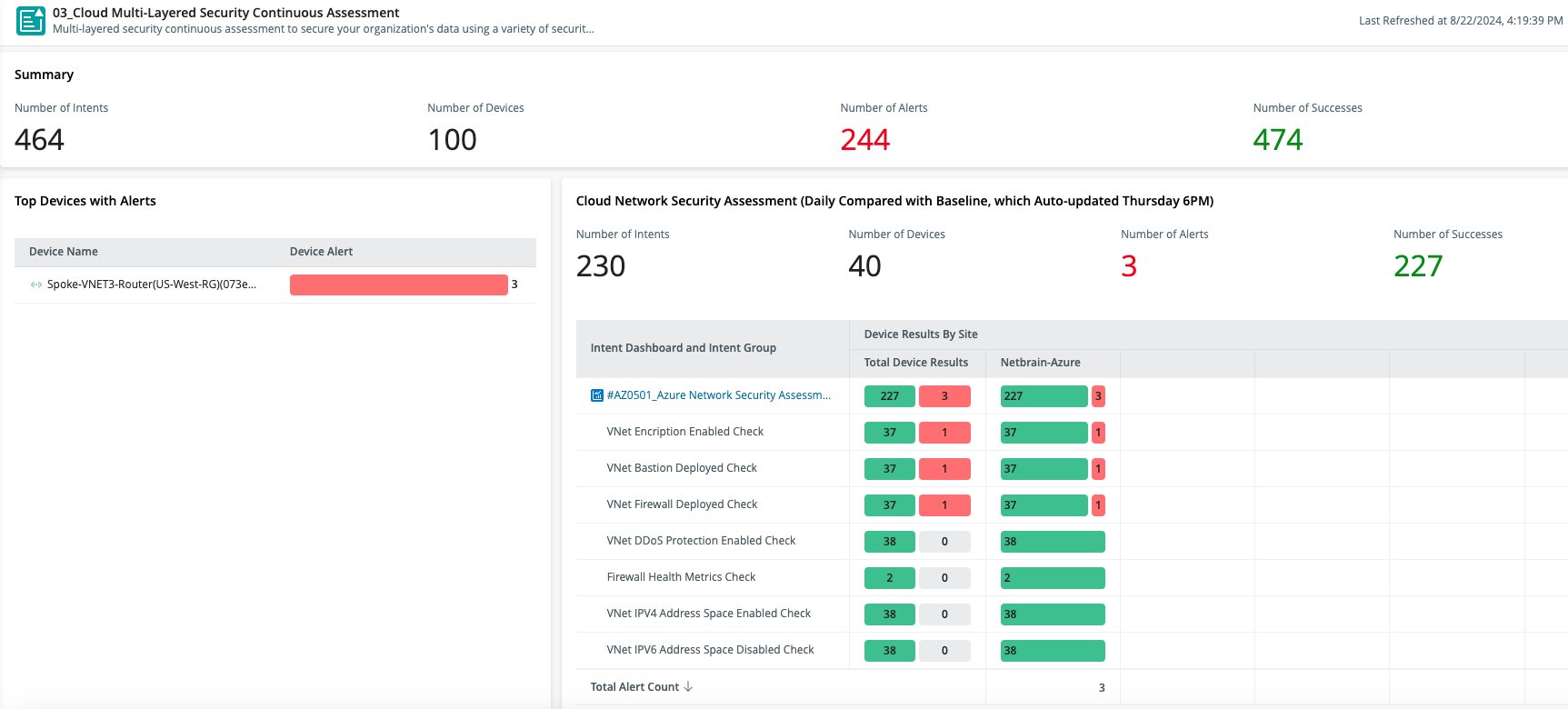
Cloud Network Security
NetBrain raises the bar for cloud security. From network layers to applications, NetBrain delivers in-depth security assessments that expose vulnerabilities and keep your cloud environment airtight. Powerful API integrations provide real-time insights into risks, empowering you to act before threats emerge.
- Catch Violations Instantly: Be the first to know when a firewall rule breaks your golden security standards. Alerts ensure no misconfiguration goes unnoticed.
- See the Problem, Solve the Problem: Visualize critical security gaps on a live network map. Identify violations at a glance and take immediate action to enforce compliance.